WannaCry: A historic cyberattack
No one can escape the news of WannaCry. The IT industry has been covering this type of malware for years, but never has one campaign spread so far or infected so many computers. Read on to gain a greater understanding of what happened and how to prepare yourself for the inevitable copy cats. Ransomware review Ransomware is a specific type of malware program that either encrypts or steals valuable data and threatens to erase it or release it publicly unless a ransom is paid. We’ve been writing about this terrifying threat for years, but the true genesis of ransomware dates all the way back to 1989. This form of digital extortion has enjoyed peaks and troughs in popularity since then, but never has it been as dangerous as it is now. In 2015, the FBI reported a huge spike in the popularity of ransomware, and healthcare providers became common targets because of the private and time-sensitive nature of their hosted data. The trend got even worse, and by the end of 2016 ransomware had become a $1 billion-a-year industry. The WannaCry ransomware Although the vast majority of ransomware programs rely on convincing users to click compromised links in emails, the WannaCry version seems to have spread via more technical security gaps. It’s still too early to be sure, but the security experts at Malwarebytes Labs believe that the reports of WannaCry being transmitted through phishing emails is simply a matter of confusion. Thousands of other ransomware versions are spread through spam email every day and distinguishing them can be difficult. By combining a Windows vulnerability recently leaked from the National Security Agency’s cyber arsenal and some simple programming to hunt down servers that interact with public networks, WannaCry spread itself further than any malware campaign has in the last 15 years. Despite infecting more than 200,000 computers in at least 150 countries, the cyberattackers have only made a fraction of what you would expect. Victims must pay the ransom in Bitcoins, a totally untraceable currency traded online. Inherent to the Bitcoin platform is a public ledger, meaning anyone can see that WannaCry’s coffers have collected a measly 1% of its victims payments. How to protect yourself for what comes next Part of the reason this ransomware failed to scare users into paying up is because it was so poorly made. Within a day of its release, the self-propagating portion of its programming was brought to a halt by an individual unsure of why it included a 42-character URL that led to an unregistered domain. Once he registered the web address for himself, WannaCry stopped spreading. Unfortunately, that doesn’t help the thousands that were already infected. And it definitely doesn’t give you an excuse to ignore what cybersecurity experts are saying, “This is only the beginning.” WannaCry was so poorly written, it’s amazing it made it as far as it did. And considering it would’ve made hundreds of millions of dollars if it was created by more capable programmers, your organization needs to prepare for the next global cyberattack. Every single day it should be your goal to complete the following: Thorough reviews of reports from basic perimeter security solutions. Antivirus software, hardware firewalls, and intrusion prevention systems log hundreds of amateur attempts on your network security every day; critical vulnerabilities can be gleaned from these documents. Check for updates and security patches for every single piece of software in your office, from accounting apps to operating systems. Computers with the latest updates from Microsoft were totally safe from WannaCry, which should be motivation to never again click “Remind me later.” Social engineering and phishing may not have been factors this time around, but training employees to recognize suspicious links is a surefire strategy for avoiding the thousands of other malware strains that threaten your business. Revisiting these strategies every single day may seem a bit much, but we’ve been in the industry long enough to know that it takes only one mistake to bring your operations to a halt. For daily monitoring and support, plus industry-leading cybersecurity advice, call us today. Published with permission from TechAdvisory.org. Source.
How to defend against WannaCry

Both businesses and individuals across dozens of countries are scrambling to fix their computer systems after a ransomware, named WannaCry, caused major disruptions earlier this month. Like most ransomware, WannaCry encrypts files and demands a Bitcoin payment for their release. What’s worse, more WannaCry variants will likely be developed in the near future, according to security researchers. Fortunately, there are some common strategies you can use to mitigate the damage of the ransomware. Update your software The first (and probably best) defense against WannaCry ransomware is to update your operating system. New research from Kaspersky shows that machines running Windows XP, 7 and outdated Windows 10 versions were affected by the ransomware. To check whether your systems are up to date, open your Windows search bar, look for Windows Update, click Check for Updates, and install any major updates. Also, don’t forget to download the latest security patches for your business applications and security software. Run security programs Many antivirus programs now have mechanisms for detecting and blocking WannaCry malware; so when you’ve fully updated your security software, run a full system scan. Keep in mind that antivirus isn’t a foolproof security solution. Instead, run it alongside other security applications like intrusion prevention systems and firewalls. Use data backup and recovery tools If WannaCry does infect your computers, only a solid data backup and recovery solution can save your business. Before ransomware strikes, periodically back up your files in both an external hard drive and a cloud-based backup service. External hard drives will serve as your local backup solution for quick recovery times. However, we recommend keeping the external drive disconnected when it’s not being used and plugging it in only when you need to back up files at the end of the day. This is because when ransomware infects a computer, it will usually look to encrypt local backup drives as well. Cloud-based backups, on the other hand, allow you to store files in remote data centers and access them from any internet-enabled device. When selecting a cloud services provider, make sure they provide the appropriate cloud protections to your files. For example, your backup vendor should provide reporting tools to keep track of any anomalies in your files. Document versioning features are also important. This allows you to recover older versions of a document in case the current version is encrypted. After your local and cloud backups are set up, perform regular tests to ensure your disaster recovery plan works. Stay informed Finally, it’s important to stay on guard at all times. WannaCry is just one of many ransomware strains affecting businesses today, and in order to stay safe you need to be constantly up to date on the latest cybersecurity- and business continuity-related news. For more ransomware prevention tips and services, call us today. We’ll make sure hackers don’t hold your business hostage. Published with permission from TechAdvisory.org. Source.
Web browser cybersecurity, ranked

Cybersecurity didn’t become more important in light of the WannaCry ransomware epidemic, it just became more visible to the average internet user. If like so many others, you’re auditing the security of business’s software, web browsers are a great place to start. Learn more about how your browser choice stacks up in your security comparison. Microsoft Internet Explorer (IE)/Edge Despite their nearly identical logos, Edge and IE are actually different browsers with vastly different security strategies. Microsoft’s legacy browser, IE, isn’t even fully supported anymore. The most recent version still gets occasional updates, but experts don’t expect that to last for long. If any website or services claims to require IE to run, consider that a possible red flag. Windows 10’s default browser, Edge, is a different story. This browser uses a technology called virtualization to create safe spaces to open and test links before granting a website’s programming code full access to a computer and user. Edge is based on the same software as IE, and the majority of its security improvements come from scrapping the browser’s customizability. If you’re okay with a fairly inflexible browsing experience, Edge is a good option. Apple Safari Safari is to Macintosh computers what IE is to Windows machines. Safari comes pre-installed on OS X and it has a long history of battling malware. Its security programming has been bested a number of times, but usually in research settings. The commonly held belief is that Safari just doesn’t have enough users to make it a profitable target. Apple has a history of responding quickly to malware, but we don’t recommend leaving anything to chance. Mozilla Firefox One of the earlier third-party web browsers to gain popularity was Firefox. Unfortunately, it just can’t keep up with the competition. In just one example, all the data from browser plugins is stored in the same location, which means a compromised add-on could easily gain access to the data stored in a password manager. One of the reasons that Firefox continues to stick around is its commitment to privacy. All the other browsers on this list profit from analyzing (and sometimes selling) your browsing habits, while Firefox has cornered the market on privacy. Security and privacy should never be confused, but if the latter is more important to you and you aren’t installing third-party plugins, Mozilla is an OK option. Google Chrome Chrome is used by almost two-thirds of all internet users, and for good reason. Like Edge, Chrome also uses virtualization to create a quarantined space between the internet and your computer. Additionally, Google issues routine security updates to its browser more frequently than any of the others on this list. There is near unanimous consent among experts that Chrome is the safest of all web browsers. Privacy however, is a whole other ball game. Pretty much every action you take using the Chrome browser is tracked, stored and analyzed. That’s not to say that your email isn’t encrypted or your saved passwords aren’t safe, it just means you have much less control over your internet identity. Being aware of how your web browser stacks up against its competitors is only a fraction of the battle. WannaCry spread to uninfected systems through a gap in the Windows security framework, and most other ransomware infections prey on human error. What your business needs is a comprehensive security audit. For more information, call us today. Published with permission from TechAdvisory.org. Source.
4 Tips for better server management

With so much technology moving to the cloud, onsite servers aren’t getting as much attention as they used to. Optimizing this critical piece of business technology is no small task, but there are a few simple things you can do to ensure the success of your in-house servers. Mount your servers properly Small businesses are usually forced to prioritize the here and now over long-term planning. Not for lack of caring, it’s just a fact of working on tight budgets and with small teams. This is especially evident when it comes to server planning. When your business first sets up shop, it’s tempting to plug in a server right next to your workstations — but doing so puts your hardware in harm’s way. Mounting servers in a rack protects them from the accidents commonly associated with highly trafficked areas: spills, crumbs and tripping hazards. Server racks keep your most essential hardware safe by organizing everything in a space that is more accessible for cleaning and management but less exposed to the day-to-day wear and tear of your office. Server planning is all about leaving room for the future. When choosing your rack mount, make sure to leave room for the hardware you will need to expand in the future. Unless office space is a serious concern, it’s better to have a half-empty server rack than to be forced to tear the whole thing down and redesign it the moment you need to expand. Keep servers separate from the main area Depending on what type of servers you are running, they can create quite a bit of noise. This coupled with the fact that they are comprised of valuable hardware means that you should do everything in your power to keep your servers physically separate from your working space. If you don’t have room for a server room, consider investing a little extra in a secure rack mount with built-in sound reduction. Never skimp on cooling Even when your business first opens its doors, server cooling is a crucial consideration. These computers are designed to work at peak capacity and need optimal conditions to do so efficiently. Even if your equipment seems to be performing just fine, too much heat can drastically reduce its lifespan. Make sure that your cooling solution operates outside the confines of your building’s infrastructure. If the central air gets shut off at night, or if your office experiences power outages, you need a cooling solution that switches over to backup power with your servers. Keep wiring neatly arranged For anyone without hands-on experience with server hardware, the number of wires going into and out of your setup is shocking. Getting the whole mess organized isn’t just about cleanliness, it also affects the performance of your current setup and the viability of installing future upgrades. Any time you are installing, removing, or rearranging your server cables, check that everything is neatly labeled and safely grouped together. Managing any type of hardware comes with dozens of important considerations, and that goes doubly so for servers. The best way to guarantee your IT investments are getting the care they require is by partnering with a managed IT services provider. To learn more about our services, give us a call today. Published with permission from TechAdvisory.org. Source.
More security features for Office 365

Microsoft has commercially released new products and upgrades that will secure company information. The threat intelligence and data governance features are designed for businesses that adhere to strict regulatory guidelines and need an extra layer of protection against cyberattacks. Here’s a detailed look at what these additions can do for your business. Threat Intelligence Threat Intelligence for Office 365 gathers data from Microsoft security databases, Office clients, email, and other recorded security incidents to detect various cyberattacks. This feature gives users in-depth knowledge about prevalent malware strains and real-time breach information to analyze the severity of certain attacks. What’s more, Threat Intelligence comes with customizable threat alert notifications and easy-to-use remediation options for dealing with suspicious content. Advanced Threat Protection (ATP) upgrades In addition to Threat Intelligence, Office 365’s ATP service now has a revamped reporting dashboard that displays security insights across a company. This includes a security summary of what types of malware and spam were sent to your organization, and which ones were blocked. According to Microsoft, these reports will help you assess the effectiveness of your current security infrastructure. ATP also has a new capability called “Safe Links” which defends against potentially malicious links in emails and embedded in Excel, Word, and PowerPoint files. If suspicious links are discovered, the user will be redirected to a warning page to avoid an infection. Advanced Data Governance The newly released Advanced Data Governance feature is also a much needed enhancement for highly-regulated companies. It classifies files based on user interaction, age, and type, and recommends general data retention and deletion policy recommendations. If, for example, your business has retained credit card data for longer than necessary, Advanced Data Governance will alert you of the possible data governance risks. Data loss prevention enhancements Last but not least, the Office 365 Security & Compliance Center is also receiving data loss prevention upgrades. With it, you can easily access and customize app permissions and control device and content security policies. So if someone in your company attempts to leak sensitive customer information, Office 365 will notify your administrators immediately. Although all these features are available only for Office 365 Enterprise E5 subscribers, security- and compliance-conscious companies definitely need these upgrades. Get the right Office 365 subscription by contacting us today. Published with permission from TechAdvisory.org. Source.
The most advanced Gmail phishing scam yet
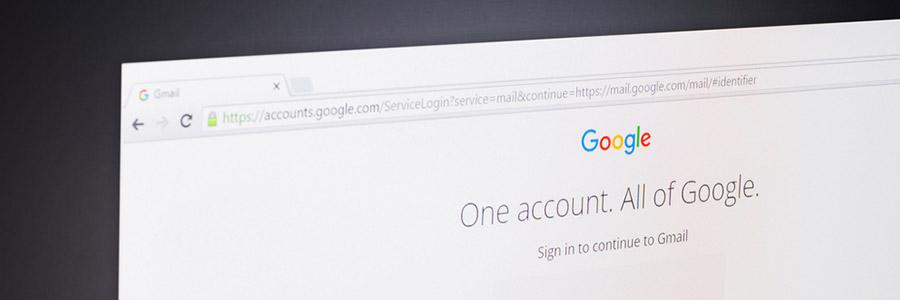
As the technology that recognizes and thwarts malware becomes more advanced, hackers are finding it much easier to trick overly trusting humans to do their dirty work for them. Known as social engineering, it’s a dangerous trend that is becoming increasingly prevalent. Read on to educate yourself on how to avoid the most recent scam and those that came before it. Broadly defined, “phishing” is any form of fraud in which an attacker tries to learn information such as login credentials or account information by masquerading as a reputable entity or person in email, IM or other communication channels. These messages prey on users who click links, images and buttons without thoroughly investigating where they lead to. Sometimes the scam is as simple as an image with a government emblem on it that links to a website containing malware. Just hovering your mouse over the image would be enough to see through it. But some phishing schemes are far more difficult to recognize. The Google Defender scam Recently, an email spread to millions of Gmail accounts that almost perfectly imitated a message from Google. The text read: “Our security system detected several unexpected sign-in attempts on your account. To improve your account safety use our new official application “Google Defender”. Below that was a button to “Install Google Defender”. What made this scheme so hard to detect is that the button actually links to a totally legitimate site…within Google’s own framework. When third-party app developers create Gmail integrations, Google directs users to an in-house security page that essentially says, “By clicking this you are giving Google Defender access to your entire inbox. Are you sure you want to do this?” Even to wary users, the original message looks like it came from Google. And the link took them to a legitimate Google security page — anyone could have fallen for it. The Gmail team immediately began assuring users that they were aware of the scam and working on eradicating it and any potential copycats. There’s no happy ending to this story. Although vendors and cybersecurity experts were able to respond to the crisis on the same day it was released, millions of accounts were still affected. The best way to prepare your business is with thorough employee training and disaster recovery plans that are prepared to respond to a breach. To find out how we can protect your business, call today. Published with permission from TechAdvisory.org. Source.
Make your SMB stand out on social media

To truly make an impression on consumers, small- and medium-sized businesses are pulling out all the stops. Standing out from your competitors could increase your chances of earning revenue. Many SMBs are now turning to social media and content marketing strategies to gain a competitive edge. Stay one step ahead of the rest with these tips: Come up with and implement a media crisis management plan It’s normal for businesses to go through a crisis or two. Avoid embarrassing public relations nightmares by having a social media crisis management plan in place and ready for implementation. Create buyer personas Social media data is a great tool to gather information about your potential customers, and in doing so, create buyer personas. Buyer personas are comprised of generalized characters that help build an ideal picture of your business in the market. Key demographic information includes age, location, and even reasons for buying and product-related concerns. Track the impact of your content marketing When it comes to content marketing efforts like blogging and social media, it’s essential to have a system to measure results. You can measure how these efforts impact your brand awareness by using metrics such as social media reach, brand mentions, media mentions, and branded searches. Integrate user-generated content on social media Businesses can utilize social media as a way to interact with consumers. This includes sharing some of their content on your own channels. Not only are user-generated content more cost-efficient, they also shorten the customer’s path to purchase. Use Hootsuite to manage Twitter chats A Twitter Chat happens when you use Twitter to talk about a common interest with others during a preset time. It’s like an online chatroom where you add to the discussion by tweeting. Efficiently managing tweets and responses is integral. Fortunately, applications like Hootsuite simplifies the whole process. It easily monitors, searches, and saves Twitter Chats onto the Hootsuite dashboard for future reference. Create better live broadcasts Livestreaming on social media platforms such as Facebook, Periscope, and Instagram is quickly gaining popularity. Before starting a livestream for your business, take time out to practice and prepare an outline before you roll the cameras. Don’t forget to promote it prior to the broadcast, and make sure you come up with a short and catchy video description. All small- and medium-sized businesses are fighting for the same thing: the consumer’s attention. Business owners can’t afford to just blend into the background; if you don’t make a good, lasting impression, you might lose out on an opportunity to make money. And if you’re relying on social media and content marketing strategies to help you, make sure you are doing it right. If you have further questions, feel free to contact us! Published with permission from TechAdvisory.org. Source.
Ugly websites cost your business big time

Good things come to those who wait, and this is especially true for small- and medium-sized businesses that plan on creating an eCommerce website. According to Vistaprint’s study on 1,800 consumers, 42 percent of respondents are “very unlikely” to buy from unprofessional or ugly websites. Go through your site and ensure everything is in order. These key indicators might help: A variety of clean photos Always take photos under professional lighting to really get the best images of your products. When customers are browsing, it’s normal for them to want to see as much detail as possible, so try to include as many photos, from as many angles your prospects might want. Clear descriptions The last thing you want to do is to confuse your customers. That’s why it’s important to include all of your products’ technical information and dimensions before creating simple and straightforward product descriptions. Establish policies Returns and refunds are an inevitable part of online shopping. In fact, a large percentage of online shoppers make purchase decisions based solely on how streamlined the returns policy is. Make sure to establish clear policies for returning and refunding items that are easy to find for customers. About page Customers unfamiliar with your brand need a story they can relate to on your website. In your About Us page, include information on who you are and what you do that sets you apart from the competition. Whatever you write, make it accessible from any page on your site. Navigation Fix broken links, make navigation straightforward, and remove outdated pages. You can’t sell 404 pages to customers, and if your site doesn’t make it easy to find what they’re looking for, game over. Design Not everyone is a web design expert, luckily you can always hire one. If your budget is tight, there are DIY site builders specifically geared toward small businesses. Or with a relatively low monthly expenditure, you can hire a managed website provider. With more revenue originating online, small- and medium-sized-business owners can’t afford to overlook the importance of creating a fully functional eCommerce website. Prior to going live, it’s essential to go through your entire site and resolve any mistakes before consumers see them. For further information on completing eCommerce websites, feel free to call us today! Published with permission from TechAdvisory.org. Source.
The cloud is more secure than you think

Even to this day, the perception of cloud technology suffers from a reputation for bad security. But as time goes on we’re beginning to see that cloud security is almost always better than that of local area networks. So whether you’re considering a cloud web server or internet-based productivity software, take a minute to learn why the cloud your best option. Hands-on management Unless you have an overinflated budget, relying on local copies of data and software means IT staff are forced to spread themselves across a bevy of different technologies. For example, one or two in-house tech support employees can’t become experts in one service or solution without sacrificing others. If they focus on just cybersecurity, the quality of hardware maintenance and helpdesk service are going to take a nosedive. However, Cloud Service Providers (CSPs) benefit from economies of scale. CSPs maintain tens, sometimes thousands, of servers and can hire technicians who specialize in every subset of cloud technology. Fewer vulnerabilities Cloud security isn’t superior just because more technicians are watching over servers. When all the facets of your business’s IT are in one place, the vulnerabilities associated with each technology get mixed together to drastically increase your risk exposure. For example, a server sitting on the same network as workstations could be compromised by an employee downloading malware. And this exposure extends to physical security as well. The more employees you have who aren’t trained in cyber security, the more likely it is that one of them will leave a server room unlocked or unsecured. CSPs exist solely to provide their clients with cloud services. There are no untrained employees and there are significantly fewer access points to the network. Business continuity The same technology that allows you to access data from anywhere in the world also allows you to erect a wall between your local network and your data backups. Most modern iterations of malware are programmed to aggressively replicate themselves, and the best way to combat this is by quarantining your backups in the cloud. This is commonly referred to as data redundancy in the cybersecurity world, and nowhere is it as easy to achieve as in the cloud. The cloud doesn’t only keep your data safe from the spread of malware, it also keeps data safe from natural and manmade disasters. When data is stored in the cloud, employees will still have access to it in the event that your local workstations or servers go down. The cloud has come a long way over the years. It’s not just the security that has gotten better; customized software, platforms and half a dozen other services can be delivered via the cloud. Whatever it is you need, we can secure and manage it for you. Call us today. Published with permission from TechAdvisory.org. Source.
Extending your laptop’s battery life

Whether you prefer a quick fix or a long-term solution, extending your laptop’s battery life should be among your priorities if you’re a heavy laptop user. Replacing an old battery with a new one or purchasing a new laptop shouldn’t be your only options, especially if you operate a business with limited resources. Here are some more economical ways to extend your laptop’s battery life. Manage your laptop’s power settings Computer manufacturers are aware that battery life is an important consideration for most users, which is why many Windows and Apple computers have settings that help reduce battery consumption. Windows laptops have a Power Plan setting that lets you choose either a standard setting or a customized power plan; Energy Saver under MacOS’ ‘System Preferences’ offers a setting that allows you to adjust display and sleep controls. Adjust display and system settings You can also make adjustments to your laptop’s display and system settings to reduce brightness, turn off screensaver, disable Bluetooth and Wi-Fi (when they’re not used), and trigger the system to hibernate instead of sleep. A “sleeping” laptop consumes a little energy, but a “hibernating” laptop consumes absolutely none. Use a battery monitor and other maintenance tools If you think your laptop battery drains unusually fast, access your system’s battery maintenance tool to check its status. If your laptop doesn’t have one, you can download an application that creates a battery health report. That report will include charge cycle count, which determines the number of charge cycles your laptop has; and battery life estimate, which states how much longer the battery will provide power based on its current settings. Keep your laptop operating efficiently One way to accomplish this is by managing your web browser usage. Having many tabs opened on your browser drains your battery’s power and reduces your productivity. If you really must have a handful of tabs opened, consider switching to power-saving browsers such as Windows Edge or Opera. When multitasking, close unused apps and programs — especially those that download files or play media, as they consume the most power. This not only helps reduce battery consumption, but also helps the user stay focused on the task at hand. Handle your laptop with care Laptops are delicate and require safe handling and a cool temperature. With the exception of a few models (e.g., Apple’s MacBook Air), many devices are designed with a cooling system that keeps its CPU, graphics processor, and other components from overheating; and not to mention, its battery from depleting fast. For that reason, handling your laptop with great care ensures longer battery life and better overall performance. When using your laptop on-the-go, make sure you don’t block its vents from circulating air, which means you should never put it on a surface such as a bed or similar soft surface that could prevent its cooling fans from working. And while it may seem harmless — and appropriate — putting your laptop on your lap is actually unsafe. For businesses with remote workers and/or bring your own device (BYOD) policies, a laptop that lasts all day allows employees to be more productive and saves your company from having to spend on new laptops or replace batteries as a result of neglect. For cost-effective strategies on business technology, call us today. Published with permission from TechAdvisory.org. Source.
