What you need to know about Mac ransomware

New strains of ransomware usually impact many Windows users, while only a small percentage of Mac users get affected. However, there are ransomware strains that specifically target Apple’s computers. Defending against these threats is crucial if your business mostly uses Macs. Here’s what you need to know about Mac ransomware. What is Mac ransomware? Ransomware is a type of malicious software that holds computer systems hostage until a ransom is paid in gift cards, or cryptocurrency like Bitcoin or Ethereum. It’s typically distributed using phishing emails, but it can also spread via unsecured networks. When Macs are infected by ransomware, users won’t be able to access their data since it’s encrypted. Ransomware messages may also threaten to release the information to the public or destroy sensitive data if victims don’t pay within a certain deadline. Healthcare and finance organizations, in particular, are more likely to pay the ransom because these organizations tend to have a lot of valuable assets, including money, and can’t afford to lose access to their critical data. Types of Mac ransomware In 2016, the KeRanger ransomware was distributed through the popular BitTorrent app Transmission. KeRanger was signed with an authorized security certificate, allowing it to evade macOS’s built-in security measures and infect more than 7,000 Mac computers. Patcher was another strain of Mac ransomware that was discovered in 2017. This type of ransomware disguised itself as a patching app for programs like Microsoft Office. When launched, Patcher would encrypt files in user directories and ask for a ransom paid in Bitcoin. But the ransomware was poorly built, so there was no way to retrieve the decryption key once the ransom was paid. In 2019, the EvilQuest ransomware encrypted files and tried to trick users into paying a Bitcoin ransom. Much like Patcher, however, there was no feature to decrypt files after paying, leaving those who paid the ransom with nothing. Ransomware attacks like these can make a resurgence at any time, which is why you need to be prepared in case of an attack. An ounce of prevention goes a long way Preventive measures are the best way to keep your Macs safe from ransomware. This involves updating your software regularly to defend against the latest threats and only installing programs from the official App Store. Since ransomware initially infects computers using phishing emails, make sure to avoid suspicious links and email attachments. Always be on alert even if the email appears to come from a legitimate company or someone you know. You must also maintain offline backups and have a disaster recovery plan to keep your business running in the off chance that ransomware successfully infiltrates your systems. Responding to ransomware If your Mac is infected with ransomware, do not pay the ransom fee, as there’s no guarantee that hackers will provide a decryption key and release your data even if you give in to their demands. Instead, use an up-to-date anti-malware program to remove ransomware from your computer. Cybersecurity experts may also release free ransomware decryptor tools to remove the infection, so keep an eye out for these on the internet. If these programs and tools don’t work, contain the spread of the ransomware by disconnecting from the network and run data recovery procedures, provided you’ve backed up your data in an external hard drive or the cloud. Mac ransomware attacks may not be common, but they still pose a great threat to your business. If you need more guidance, contact our team of security experts today. We stay abreast of the latest Mac security threats and know just how to keep your business safe. Published with permission from TechAdvisory.org. Source.
Data storage: HDD and SSD defined
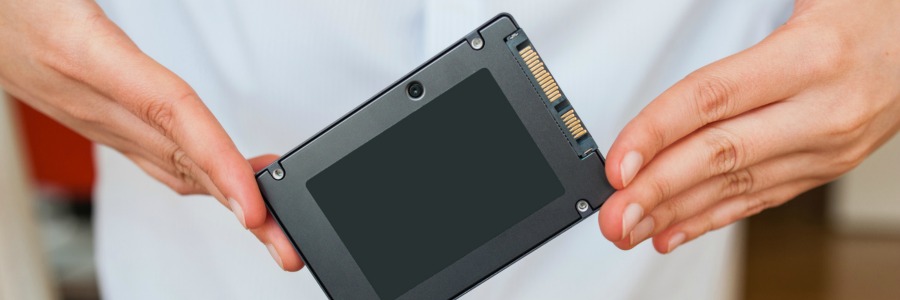
When purchasing new computers, buyers used to have limited choices when it came to what kind of storage they got with their laptop or desktop PCs. But nowadays you can configure your system with either traditional hard disk drives (HDDs), increasingly common solid state drives (SSDs), or in some cases both. Here’s a comparison of both storage drives so you can figure out which best suits your needs. What is an HDD? An HDD is basically a storage device in a computer. It consists of metal platters with magnetic coating, a spindle, and various moving parts to process and store data. The common size for laptop hard drives is the 2.5” model, while a larger 3.5” model is usually found in desktop computers. What is an SSD? An SSD is another type of data storage that performs the same job as an HDD. But instead of storing data in a magnetic coating on top of platters, an SSD uses flash memory chips and an embedded processor to store, retrieve, and cache data. It is roughly about the same size as a typical HDD, and resembles smartphone batteries. HDD and SSD comparison The differences in capabilities between the two storage devices can be grouped into six categories: 1. Speed This is where SSDs truly prevail. While HDDs need a long time to access data and files because the disk must spin to find it, SSDs can complete this task 200% faster since data is instantly accessed through flash memory chips. This is why an SSD-equipped PC will boot operating systems within seconds and deliver blazing-fast speed for launching programs and applications, whereas a computer that uses an HDD will take a much longer time to boot the operating system, and will continue to perform slower than an SSD during normal use. 2. Capacity The largest SSD units have a maximum 100 TB storage capacity. Although there are large SSDs, anything that’s over 1 TB will cost businesses a lot of money. HDDs, on the other hand, have much larger capacities available for much more affordable prices. 3. Durability HDDs consist of various moving parts and components, making them susceptible to shock and damage. The longer you use your HDD, the more it wears down and most eventually end up failing. Meanwhile, an SSD uses a nonmechanical design of flash storage mounted on a circuit board, providing better performance and reliability, and making it more likely to keep your files and data safe. 4. Noise An HDD can sometimes be the loudest part of your computer. Even the highest-performing HDDs will emit some noise when the drive is spinning back and forth to process data. SSDs have no moving parts, meaning it makes no noise at all. 5. Heat More moving parts means more heat, and HDD users will have to live with the fact that their device will degenerate over time. SSD uses flash memory, generating less heat, helping to increase its lifespan. 6. Cost SSDs are generally much more expensive than HDDs for the same capacity. This is why many budget laptops may only have up to 512 GB of SSD storage. Despite the high costs and low capacity, however, SSDs are the clear winner over HDDs in terms of performance. While you’re paying more for less memory with an SSD, you’re investing in a faster and far more durable data storage option in the long run. We recommend using an SSD as the primary storage for your operating system, applications, and most-used programs. Many laptops and computers also allow you to install additional SSDs, so you can upgrade as required if your storage needs grow. Implementing HDD as a secondary storage unit is another great idea, especially if you need a place to store documents and pictures because they don’t need to leverage the incredible access times and speeds of an SSD. Looking to invest in some new hardware for your business? Talk with our experts before you make a decision. We can provide sound advice and help guide you in the right direction. Published with permission from TechAdvisory.org. Source.
Engaging on-hold messages via VoIP

When an operator asks a client for permission to put them on hold, what they’re really saying is “Can you wait a short time not talking to anybody?” A caller can be put on hold at different times throughout a call, and for varying durations. This lull used to be insufferable, but now you can improve customers’ on-hold experience with Voice over Internet Protocol (VoIP). VoIP phone systems help make waiting on the line bearable or even downright enjoyable via the sharing of fun anecdotes and info, playing of on-brand music, and the conveyance of engaging messages. Information Providing customers with new information and intriguing anecdotes will keep them from thinking that they aren’t being served — when, in fact, you are hard at work addressing their concerns at the other end of the line! You can also initiate a playful trivia or “Did you know?” kind of contest where providing a correct answer once the call resumes wins them a prize. Music Callers who hear music while on hold tend to stay on the line compared to those who experience silence. While traditional phone systems also have a music on hold feature, VoIP services enhance this feature and offer more options. Instead of being limited to legacy tools’ music loops, VoIP systems let you easily upload your audio of choice. Just a couple of tips: use music that suits your brand, and take your clientele’s demographics into account. The upbeat music that a sporting goods brand uses might not work for an investment bank. With VoIP systems, you can customize the frequency and duration of a track and configure whether the music restarts or continues where it left off when a caller is placed back on hold. You can also set the order of different tracks or randomize them for callers. Messages Customers who are put on hold are captive audiences for your marketing messages. VoIP systems let you record a variety of messages for different numbers according to the purpose of the caller. For example, if the caller wants to get in touch with the sales department, the on-hold message could inform them of current special offers, promotions, or sales. “Hold message” scripts that utilize your company’s TV and radio ads might elicit an “I think I’ve heard this somewhere before” response. Conversely, you could put a totally new spin on the usual tone and style of your marketing messages and really get creative with humorous advertisements that make your customers chuckle. A little bit of levity never hurt nobody! For the service department, you can use messages that assure the customer that an agent is taking care of their concerns. Using a service-appropriate message makes them feel like they’re getting personalized care. The rich on-hold functionality of VoIP systems allows you to turn the on-hold experience into a positive customer service experience. Make sure this window of opportunity is taken full advantage of. Get in touch with us today and we’ll help you increase the odds that your clients will happily stay on the line and continue to do business with you. Published with permission from TechAdvisory.org. Source.
Is your web browser safe enough?

Web browsers are gateways to the internet, which is why you should care about how they transmit and store sensitive information. In an era where too much security is never enough, you need your browser to also have built-in cybersecurity features. But which web browser is the safest? Read on. Microsoft Edge Microsoft Edge, Windows 10’s current default browser, is an improvement over its predecessor Internet Explorer (IE). Edge is based on the open source Chromium browser, resulting in a powerful and efficient browser that supports Progressive Web Apps and Google Chrome extensions. Edge’s main advantage is that it is Windows 10 co mputers’ native browser, which means it should integrate more seamlessly with the Windows OS ecosystem in terms of power usage and data security. It uses Windows Defender SmartScreen to protect users from phishing and malware attacks. And it has a three-level defense against third-party trackers, allowing users to choose between Basic, Balanced, and Strict levels of blocking trackers from collecting personal data and monitoring browsing behavior. Safari Safari is a graphical web browser developed by Apple for iOS, iPad OS, and macOS. The current iteration is Safari 14, released September in 2020 alongside macOS Big Sur, and it’s also compatible with Catalina and Mojave. Safari has long been using a system called Intelligent Tracking Prevention (ITP) that identifies and prohibits trackers from accessing a user’s personal data. Safari 14’s Privacy Report feature shows all the trackers ITP has blocked. Safari also has secure password monitoring, which notifies users if any of their saved passwords in iCloud shows up in a data breach. The browser, however, is only available on Apple devices, with full capabilities found only on MacBooks and Macs. Mozilla Firefox Mozilla Firefox is a free and open-source web browser developed by the Mozilla Foundation. It is widely available across platforms, even on Unix and Unix-like operating systems such as FreeBSD, OpenBSD, illumos, and Solaris Unix. Because of Firefox’s open-source development platform, it can be quite unsecure to use on public computers. For personal and single-user business devices, however, Firefox is relatively safe, especially once all security features are activated and tweaked to your needs. Some key features include a password manager called Firefox Lockwise, a third-party tracker protection system, Private Browsing, and Firefox Monitor, which checks if your email address has been compromised in a data breach. Mozilla also has a Bug Bounty program, which offers a financial reward to anyone who can identify gaps and holes in Firefox code, so the browser can be patched and improved as urgently as possible. Mozilla also promises no legal action against anyone who complies in good faith under its Bug Bounty program, including any claim under the DMCA for circumventing technological measures. Google Chrome Google Chrome is a cross-platform web browser developed by Google. It is the default browser for Google’s line of laptops and third-party Chromebooks. Chrome utilizes a process allocation model to sandbox tabs. Sandboxing is a security mechanism for separating running programs to keep software vulnerabilities from spreading. Chrome also regularly updates two sets of blacklists, one for phishing and one for malware, which it uses to warn users of potentially harmful sites. It also touts site isolation and predictive phishing protection features that receive regular and critical updates every six weeks and within 24 hours of a threat being discovered, respectively. Being aware of how your web browser stacks up against the competition is only half the battle. Ransomware like WannaCry can spread to uninfected systems through a gap in the Windows security framework, and most other malware infections prey on human error. What your business needs is a comprehensive security audit. For more information, call us today. Published with permission from TechAdvisory.org. Source.
What are Microsoft 365 Groups connectors?

Microsoft 365 Groups is a cross-application service that lets users choose the people with whom they want to collaborate and share resources, such as a document library or a Microsoft Outlook inbox. And with its connectors feature, anyone can send information — even those from third-party apps — to the rest of the group right in their shared inbox. Read on to learn more about what connectors are and how they can help your team be more productive. How do connectors work? Connectors enable users to access third-party apps and services within their Outlook groups, eliminating the need to scour through dozens of tabs to open a specific application. For example, your staff can keep tabs on a particular hashtag your company is following on Twitter without having to open the app in another tab. They can also receive the latest news and current events by adding the Bing News connector, or keep track of projects by connecting to Trello or Asana. Content and updates from connected apps and services are delivered via connector cards, which offer a user-friendly way to interact with external applications. If a particular connector is added to a Group, connector cards are generated within the group’s activity feed. While most cards will display events in plain text, some applications like Twitter and Trello provide actionable messages. Trello, for example, allows you to assign or comment on an event card — which you can do without leaving Outlook. Aside from configuring the apps and services to connect to, the connectors feature also allows users to set the frequency of delivery of content and updates, enabling you to better manage your Outlook inbox. Who can create a connector? Any group member can configure and use a number of connectors. Once they configure a connector for a group, that app will be made available to other members. However, only the person who added the connector can modify the settings of that app. Microsoft 365 also lets your business develop its own connectors by embedding the Connect to Microsoft 365 button on your site. This allows users to connect to your service and get updates on your company, as they would with other third-party services. Your Microsoft 365 client basically becomes a hub for third-party apps, keeping your company in sync to get more work done. How do you access Microsoft 365 connectors? Simply navigate to a Group from your Outlook page and click on the Connectors tab at the top of the page. From here, you can choose the apps and services your group needs, and connect these to any of your Outlook groups. As your business grows, you’ll need to use more apps and services to be more productive. By aggregating them all in one place, you save time shifting around apps to find the information you need. So the next time you create a Microsoft 365 Group, help your team members work more efficiently by setting up some connectors. Microsoft tools like Groups and Outlook help organizations of all sizes improve their workflows and enhance their productivity. If you’re interested in learning about Microsoft apps and what they can do for your business, contact us today. Published with permission from TechAdvisory.org. Source.
How business intelligence can help small businesses

Before, hiring specialists to analyze business data entailed costs that only large companies could afford. This was one of the reasons why small- and medium-sized businesses (SMBs) were hesitant to implement business intelligence (BI). But times have changed. SMBs now have access to a vast range of business tools that can improve data management processes. To stay ahead, SMBs should harness the capabilities of BI to develop effective business strategies using large volumes of data just sitting in their systems. Self-service BI tools are plentiful — and inexpensive The emergence of self-service BI puts useful business analytics within reach of smaller-business owners who lack the big budgets of larger corporations. In fact, there are numerous self-service BI tools that you can use to get started in this area without even spending a dime. Microsoft Power BI is a powerful and user-friendly application, and most businesses will find the functions they need in the free version. Zoho Analytics has a low entry-level cost, too, and the slightly pricier yet still affordable Tableau is another option worth exploring. You’ve already got the data you need It’s easy to underestimate the amount of data your SMB already has at its disposal. In every area of your business, from finance and sales to customer relations and website management, the software packages you use to simplify your everyday operations reap tons of information that most of us don’t even think twice about. By talking to key stakeholders in your organization’s various departments, you can get an idea of the kind of data you already have, how it’s generated, and where it’s stored. You can then utilize BI tools to transform that information into meaningful business insights that will inform your decision-making. No need for you to invest in time-consuming data generation from scratch! It’s easy to get started BI is an intimidating term, especially for the average business owner. But by taking small steps, it’s easy for anyone to get started. Before you know it, you’ll be enjoying the benefits of having data-driven, intelligence-based insights that will enable you to make better business decisions. Most self-service BI tools come with built-in suggestions for reports that businesses commonly run and find useful. Some worthwhile statistics to explore include the percentage of your clients who cancel within a given period, website landing pages that generate the longest visits, your most profitable individual products or services, the days or months in which you generate your highest revenues, and which of your clients bring in the most revenue and profit. Harnessing data is the future of the business world — it’s how companies like yours can make smarter decisions that increase efficiency and profitability. And with a trove of self-service tools available in the market, SMBs no longer need a humongous budget to reap the benefits of BI. To find out more about implementing tools that can help you do smarter business, just give us a call. Published with permission from TechAdvisory.org. Source.
What’s in store for Windows users in 2021?

If you’ve been waiting for updates on Windows 10, here’s some good news and more! Microsoft will very likely release big updates to the OS in 2021. Additionally, the tech giant is expected to introduce new services designed to maximize user experience across a wide range of devices. What’s new on Windows 10? Microsoft tends to release major updates followed by several smaller ones meant to implement minor feature changes and improvements. This likely won’t be the case in 2021. Sources indicate that the first of two updates will be released sometime in the spring next year. It will be a servicing style update similar to those released in the latter halves of 2019 (19H2) and 2020 (20H2). To illustrate, the 19H2 update included improvements in battery usage efficiency, while the 20H2 update focused on enhancing general performance and quality. The spring update (21H1) will likely be in preparation for the bigger one (21H2) coming around the fall. Next year’s major update will likely enable x86 64-bit Windows 10 to be emulated on computers that use ARM processors. This is good news if you use ARM-based computers, such as Microsoft’s very own Surface line of notebooks. With the update, you will be able to run legacy Windows programs on your device. Windows 10X Google’s Chrome OS might not be as feature-rich as Windows 10, but its lightweight nature and simple interface make it a hit among users who want a fast and straightforward operating system. That it is exclusively built into light, compact, and affordable notebooks — called Chromebooks — certainly adds to its appeal. Microsoft’s Windows 10X is purportedly its answer to Chrome OS. It’s a lightweight version of Windows 10 designed to perform well even on low- to mid-range computers. Windows 10X also boasts an updated, modern-looking interface, formidable security, and excellent battery efficiency. Like Chrome OS, Windows 10X will be exclusive to a specific line of computers which, according to reports, may include ARM-based and foldable devices. Windows 10X will likely become available in the earlier half of 2021. Cloud PC Windows 10 Cloud PC is a service that allows you to install applications to a version of Windows found on the cloud. Both the apps and the OS are streamed to your computer and use very little of the machine’s power. This makes it a great service for computers with low memory or ones that suffer from weak performance. Any apps installed via Cloud PC will appear on your Start menu as if it were installed locally on your machine. Cloud PC will likely be an integrated service with both Windows 10 and Windows 10X. Windows 10X devices likely will not come with win32 local support, although the feature may be added in a future update. You can resolve this issue by installing your win32 programs on Cloud PC and streaming them via your Windows 10X device. Microsoft has yet to confirm the exact nature and scope of their upcoming updates and services, but we can make educated guesses. In any case, it seems users can look forward to improved performance on Windows 10, as well as more opportunities to save money and get more out of their tech investments. If you need recommendations on how to take full advantage of these updates and new services, just give our experts a call. Published with permission from TechAdvisory.org. Source.
Two excellent ways to verify user identity

A secure login process is an excellent way to protect your business from cybercriminals. When it comes to verifying user identity, you can choose between two-step authentication and two-factor authentication. Learn the difference between the two so you can have a better appreciation of your cybersecurity options. If you want to improve your business’s cybersecurity, you should take a closer look at your authentication process. Two-step and two-factor authentication are two of the most commonly used authentication methods. Many businesses use the terms two-step and two-factor authentication interchangeably, but there are subtle differences between the two. Two-step authentication A two-step authentication process requires a single-factor login (such as a password or biometric reading) as well as another similar type of login credential that a user must provide. This process typically requires entering a password for the first step and entering another security code for the second step, which may be accomplished by providing a one-time code generated by an authenticator app such as Google Authenticator. Two-step authentication adds an extra step in the verification process, making it more secure than single-step authentication (i.e., providing only a password). However, if a person or business is hacked, it won’t be enough to stop hackers from getting a hold of whatever they are looking for. Two-factor authentication Two-factor authentication, a subset of multifactor authentication, is significantly more secure than two-step authentication. This type of authentication requires two different types of information to authenticate a user’s identity. For example, it could be a combination of a fingerprint or retinal scan as well as a password or passcode. Because of the additional authentication information required, hackers would have great difficulty breaking into a network using a two-factor authentication system. Which one is better? Relying on a single-factor authentication process is no longer sufficient in ensuring the safety of your network. Securing the authentication process and making it difficult for cybercriminals to access your network should be on top of your priorities. Deciding whether to use two-step or two-factor authentication largely depends on your business’s specific security requirements. To take the stress out of securing and protecting your network, call us today for expert cybersecurity advice. Published with permission from TechAdvisory.org. Source.
Should small businesses use laptops or desktops?

As an entrepreneur, you often have to make choices that can either make or break your company. One such decision you have to make is whether to in desktops or laptops. Make the best choice by assessing the current situation and taking the following things into consideration. Portability The pandemic has driven the majority of businesses to adopt remote work setups. If your business will implement a similar arrangement, investing in laptops is the smart move, as your staff can easily take their device with them anywhere they want to work. However, there may be instances when this can turn out to be counterproductive: if your employees can jump into work mode easily, they may get the impression that they have to work 24/7. As such, you must not discount desktops altogether. While laptops are light and portable, modern desktop computers aren’t nearly as immobile as they used to be. In many cases, desktop screens are thin and light, and all-in-one desktops are easy to move around. Memory and speed Before, desktop computers had more memory than laptops, and they were faster because they had bigger processors. This has now changed, thanks to improvements in laptop technology. But until high-powered laptops become affordable to the general public, desktop computers are going to provide your business with more memory, speed, and power for your money. How much speed and memory you need depends on the work you do. If your employees’ work mostly entails word processing and emailing, laptops should be enough. But if they need to run gaming software or access heavy media files, better invest in desktops. Security A desktop computer is more physically secure because it’s often kept in one location, making it easier to guard. And because a desktop’s internet access is often a single source (whether through Wi-Fi or cable), it’s easier to defend it against malware and cyberattacks. If you choose to invest in laptops, make sure to have strict policies on how to protect devices that are used outside of the office. Don’t let your staff connect to unsecured networks, and use encryption tools to protect data from unauthorized access. You must also employ mobile device management software to enable your administrator to wipe data clean off laptops should they get lost or stolen. Price Laptops, especially the smaller notebook-style ones, are a lot cheaper than desktops. However, desktop computers are also becoming more affordable through local channels and lenient payment terms. And with a capable IT services provider that can provide you with infrastructure or offer cheaper desktop options, cost probably won’t be a deciding factor. Quality Although laptop computers provide the convenience of portability, they’re prone to battery and charging cord problems. They are also easily damaged, especially if they are dropped or mishandled. By contrast, desktops are generally sturdier. But when they do experience a problem, repairing them can be expensive. Final recommendation The desktop versus laptop debate is an old one, with supporters on both sides touting the advantages of their choice. A growing company usually needs a combination of both types of computers, especially as their needs evolve. If you have questions regarding choosing the best computer for your company, give us a call. We’ll be happy to assist you in improving your business. Published with permission from TechAdvisory.org. Source.
Microsoft Teams vs. Google Meet

The use of online communication and collaboration tools has hit record highs in the past few months on account of the coronavirus-induced shift in work arrangements. Among the most popular platforms right now are Microsoft Teams and Google Meet, which allow organizations to easily connect with colleagues and clients remotely. But while both share the common capability of video calling and messaging, distinct features may make one a better option for your specific needs compared to the other. Calling features Microsoft Teams and Google Meet both offer enterprise-grade security, 1080p HD-quality video, and screen sharing capabilities, but there are some slight differences. In the free version of Microsoft Teams, there is no limit to the number of people who can use its chat and document collaboration functions. Meanwhile, up to 20 users can join an audio or a video call. This number increases to 250 in the paid version. What’s great about Microsoft Teams is it supports meeting and group call recording, and even has captions and transcription features. It also has an inline message translation feature that translates messages into the language specified in a user’s settings. On the other hand, Google Meet’s free version supports up to 100 participants in a video call. What’s more, it has intelligent built-in features like muting and auto screen focus, which automatically switches the screen to the person who is currently talking. It also lets people join meetings even without Wi-Fi or data through unique dial-in phone numbers. Integrations and add-ons Microsoft Teams is, first and foremost, a unified platform that allows users to communicate and collaborate on a single platform. It comes with powerful content collaboration on Microsoft 365 apps (e.g., Word, PowerPoint, Excel) and easily integrates with hundreds of other productivity and collaboration platforms. Meanwhile, being a Google product, Google Meet fully integrates with Google Workspace (formerly G Suite). For instance, users can schedule appointments and set call reminders within Google Meet using Google Calendar. Users can even broadcast their presentations live on YouTube. Pricing Both Microsoft Teams and Google Meet have free versions but with limited features. With the free version of Microsoft Teams, users can join a meeting and use its screen and file sharing features even without an account. However, they cannot record and save meetings. They also cannot take advantage of call encryption and call-in features if they do not have a Microsoft 365 account. The most affordable subscription is $5 per month per user, and an additional $4 per user is needed for the call-in capabilities. Adding webinar features is also an additional cost if users want to livestream events to hundreds of people. Meanwhile, users can use Google Meet for free with their personal Gmail accounts, but also with limited capabilities. A subscription that starts at $6 per month per user, however, lets users get Google Meet along with all the other powerful Google business apps and tools. What works for you? Knowing the similarities and differences between the two platforms, it should be easy for you to decide which suits your business the best. Google designed Google Meet for startups and small companies that need a low-cost communications solution, while Microsoft Teams, with its robust features, is suitable for small and large businesses alike. If you’re still unsure about either product, you can opt for a free trial to help you in making the decision. Otherwise, you can contact our team today so we can recommend a VoIP solution that’s perfect for your business. Published with permission from TechAdvisory.org. Source.
