Microsoft 365 data security: 7 Ways to boost protection

Microsoft 365 has become an incredibly popular choice for enterprises of all sizes looking for a comprehensive set of tools for staying productive and secure. But as with using any software, it is important to take steps to protect your data. In this article, we will discuss seven ways to boost data protection in Microsoft 365. We will also provide tips on how businesses and employees can stay safe online. Secure mobile devices It’s common for employees nowadays to use personal smartphones or computers to access their work email, calendar, contacts, and documents, especially if they’re working remotely. This is why securing employee-owned devices should be a critical part of protecting your organization’s data. Installing mobile device management features for Microsoft 365 enables you to manage security policies and access permissions/restrictions, and remotely wipe sensitive data from mobile devices if they’re lost or stolen. Turn on policy alerts Establish policy notifications in Microsoft’s Purview compliance portal to help you meet your company’s data security obligations. With policy alerts on, your employees will receive tips about sending confidential information anytime they’re about to send messages to contacts outside of the company network. These preemptive warnings can prevent data leaks and also educate users on safer data sharing practices. Use multifactor authentication Using only a password to protect your Microsoft 365 accounts could lead to account hijacking, which could put your data at risk of being compromised. Enable multifactor authentication (MFA) so that users will be required to supply additional credentials on top of a password before they can access their accounts. MFA makes it difficult for hackers to access your accounts since they not only have to guess user passwords, but they also need to provide a second authentication factor like a one-time SMS code or a fingerprint scan. Avoid public calendar sharing Microsoft 365’s calendar sharing feature allows employees to share and sync their schedules with their colleagues. However, publicly sharing this information exposes you to security risks because it helps attackers understand how your company works, determine who’s away, and identify vulnerable users. For instance, if security administrators are publicly listed as “Away on vacation,” an attacker may see this as an opportunity to unleash malware on unattended computers. Apply session timeouts Many employees usually forget to log out of their Microsoft 365 accounts and keep their computers or mobile devices unlocked. This could give unauthorized users unfettered access to company accounts, allowing them to steal sensitive data. By applying session timeouts to Microsoft 365 accounts, email accounts, and internal networks, users will be automatically logged out after a period of inactivity. This can prevent hackers from taking over users’ devices and accessing private information. Employ role-based access controls Access management is another Microsoft 365 feature that will limit the flow of sensitive data across your organization. It lets you determine which users have access to specific files in your company. For example, rank-and-file employees won’t be able to read or edit executive-level documents, thus minimizing the risk of data leaks. Encrypt emails Encrypting classified information is your last line of defense against data breaches. If hackers intercept your emails, encryption tools will make files unreadable to unauthorized recipients. This is a must-have for Microsoft 365, where files and emails are shared on a regular basis. Partner with us to ensure your organization’s Microsoft 365 accounts are always secure and compliant with changing data security requirements. Call us today and our IT experts will help find the right cybersecurity solutions for you. Published with permission from TechAdvisory.org. Source.
Make your website stand out with these modern design trends

Nearly 94% of a visitor’s first impression of your business comes from web design. That’s why it’s critical that your website uses modern web design trends. But how can you leverage these trends to spruce up your website? Read on to learn more. Custom illustrations A popular website design trend is the use of custom illustrations instead of photography. The reason for this is that illustrated images are smaller in size and therefore will load faster than traditional photographs. Illustrations can also be a great way to convey ideas and concepts that may be harder to express with photographs. Web pages for services or causes, which usually don’t have product images, can benefit from unique illustrations to capture visitors’ attention. A good example is Alice Lee’s, which uses illustrations to highlight her various services. Dyamic scrolling effects Scrolling effects are animations that are triggered when a user scrolls down the page. They can make web experiences more dynamic and encourage visitors to keep scrolling. Engineered Floors is a good example of a website taking full advantage of scrolling effects. Scrollytelling Scrollytelling, or narrative visualization, unfolds a digital story as a user scrolls down the page. These stories can be either short bits of information or long reads with supporting images and videos that change as a visitor scrolls down the page. This design allows you to highlight your company’s products or services through engaging content to captivate visitors and entice them to make a purchase, subscribe to a mailing list, and more. A great example of scrollytelling is Infrared Mind Body. One-page websites A one-page website features a simple and straightforward design that highlights the important selling points of the products or services you want to promote. By eliminating visitors’ need to navigate multiple pages, they will likely stay on your site longer, increasing the chances of a successful purchase or subscription. FourFold Consulting is a perfect example of a good one-page website. Monochromatic layouts A monochromatic layout uses a clean, simple design with a few colored elements to catch a user’s attention. Similar to using white space, this design is ideal if you want to draw visitors to a call to action button. Check out Lemonade’s website to see how effective a monochromatic layout can be. Minimalism Minimalism uses flat design elements, such as basic geometric forms, clean text, limited color palettes, and straight lines to create a unified and functional design. A minimalist design makes it easy to book an appointment, buy items, or look for more information because there are no flashy effects or large walls of text to distract users. Additionally, websites with fewer elements load faster and improve user experience. To see how effective a minimalist website design is when done right, look at Outlab’s website. If you’re looking to incorporate these modern design trends into your website, give our expert team a call today. Published with permission from TechAdvisory.org. Source.
The advantages of using a cloud-based OMS

In today’s business world, having a cloud-based OMS can give you a big advantage. The cloud offers many benefits, including the ability to access your data from anywhere, scalability, and cost savings. A cloud-based order management system (OMS) is a great choice for eCommerce businesses. Read on to learn more about the advantages of using a cloud-based OMS. What does an OMS do? While the terms inventory management system and order management system tend to be used interchangeably, there is a difference between the two. An inventory management system helps you figure out what people want and need so you can stock up on those items. On the other hand, an order management system helps you handle the orders that are coming in in real time. A traditional OMS system is installed on a company’s own servers, so the company has full control over the system and its features. Traditional OMS systems are also generally more expensive than cloud-based systems, since they require upfront costs for hardware and software. On the other hand, a cloud-based OMS enables eCommerce businesses to track orders for goods and services from a centralized dashboard that can be accessed by your staff anytime, anywhere on any internet-connected device. In general, it can help you better organize orders into a coherent and manageable workflow by: Updating your website to reflect when certain items are out of stock Automating payment authorizations and integrating these with your shipping services Providing reports to customers about their order’s shipping status Automatically restocking products and materials once they dip below a certain level Automatically processing refunds and returns Monitoring your business while you’re on the go Storing data in a more efficient and less costly manner Ensuring your data is protected in the event of a disaster There are certain OMS platforms with unique capabilities that make them suitable for particular business structures. This makes it all the more important to find a solution that reduces the most tedious organizational tasks for tracking your store’s orders. What are the benefits of a cloud-based OMS? Using a cloud-based OMS offers several key advantages: Enhanced decision-making With a cloud-based OMS, you have all the information you need to make smarter business decisions at the tip of your fingers, including consumer behavior, market trends, and product performance. Improved visibility A cloud-based OMS offers a consolidated view of your orders and inventory in real time, allowing you to stay on top of the entire fulfillment process so you never miss a sale. This also enables you to optimize inventory levels while minimizing surplus. Additionally, an OMS gives you better visibility into your business’s processes, so you can easily identify issues and make the necessary adjustments to achieve operational efficiency. Faster delivery When a customer places an order, your cloud-based OMS will choose the warehouse or fulfillment center closest to them as well as the method of fulfillment. A fulfillment request will then be sent automatically to the warehouse so the customer’s item can be immediately prepared and shipped out. Fewer errors Using a cloud-based OMS allows you to automate various stages of order processing, eliminating the need to manually enter and update order details. This reduces the risk of error, increasing your eCommerce business’s operational efficiency. Lower costs With fewer errors, you can save time and effort as you no longer need to correct inaccurate order information. This also means your business saves on labor. And because a cloud-based OMS requires virtually no hardware, you can also eliminate installation, maintenance, repair, and other associated costs. As eCommerce continues to grow in popularity, a cloud-based OMS will become an essential tool for businesses that want to stay competitive. If you’re not already using a cloud-based OMS, now is the time to make the switch. Contact us today to learn more about this amazing tool. Published with permission from TechAdvisory.org. Source.
Here’s how to remove unwelcome notifications in Windows 11

Don’t be surprised if you see some ads while using your Windows 11 computer. Microsoft designed its operating systems to show notifications and ads, regardless of the version. Some users don’t mind the ads, but if you do and are wondering if there’s any way to remove such notifications, wonder no more. Here’s how to get rid of unwanted ads in Windows 11. Turn off suggested content in Settings You may find Microsoft subtly suggesting some of its products or services to you while you use certain built-in apps. If you don’t like that, you can disable this feature by going to Settings > Privacy & security > General. Then, toggle off the switch button beside Show me suggested content in the Settings app. With this feature off, the Settings app will stop displaying suggested content. Disable system notifications Microsoft has programmed Windows 11 to send push notifications of tips and tricks that introduce users to more of the company’s products. If you find these suggestions random or unwelcome, you can disable them entirely. Go to Settings > System > Notifications. Then, uncheck two boxes: the one beside Offer suggestions on how I can set up my device and the one beside Get tips and suggestions when I use Windows. This will prevent the system from showing notifications about certain Windows features or offers. Remove ads on the Lock screen Your Lock screen may display ads from time to time depending on your background settings. To prevent this, simply go to Settings > Personalization > Lock screen and choose either the Picture or the Slideshow option under Personalize your background. Then, scroll down the page and deselect the “Get fun facts, tips, tricks, and more on your lock screen” option. Your Lock screen should now be ad-free. Uninstall pins from the Start menu Microsoft uses the pin feature on the Start menu to place ads for its own products and services or other apps found on the Microsoft Store. The apps typically vary depending on the user’s region, but some of the common ones include Prime Video and Adobe Express. They’re designed to be highly visible to lure users into clicking and subscribing to them. To remove these pins, open Start, right-click the app you want to get rid of, then select Uninstall. Keep File Explorer ad-free Microsoft also uses File Explorer to promote certain services like OneDrive. To stop getting such ads in File Explorer, open File Explorer and click the three-dotted menu on the command bar. Choose Options, then go to the View tab. Look for the “Show sync provider notifications” option, then deselect the checkbox beside it. This turns off advertisements in File Explorer. This blog is a good starting point if you want to learn about Windows 11. But if you need something a little more advanced, our managed IT services experts are second to none. Get in touch with one of our specialists today to maximize Windows 11’s full potential. Published with permission from TechAdvisory.org. Source.
Defending against watering hole attacks

More and more cybercriminals are launching watering hole attacks to gain access to company networks. But what exactly is a watering hole attack, and how can you protect yourself from it? Read on to learn how. How watering hole attacks work The term “watering hole” colloquially refers to a social gathering place where a particular group of people often go to. As internet users, we all have unique “watering holes” or websites that we frequently visit. For example, a financial analyst is likely to visit websites related to financial investments and market trends. In a watering hole attack, cybercriminals observe the watering holes of a specific demographic and infect their targets’ most visited websites with malware. A user who has the misfortune of visiting any of these compromised sites will then have their device automatically loaded with malware. The malware used in these attacks usually collects the victim’s personal information and sends it back to the hacker’s server. In extreme cases, the hacker will also actively take control of the infected device. But how does a cybercriminal choose which websites to hack? With internet tracking tools, hackers find out which websites companies and individual users visit the most. Hackers then attempt to find vulnerabilities in those websites and embed them with malicious software. Tips to defend against this threat Hackers these days are so highly skilled that they can exploit any website using a watering hole attack. Even specific ethnic communities and demographics have become targets of this scheme. Protect yourself and your business from watering hole attacks by doing the following: Update your software Watering hole attacks often exploit security gaps and vulnerabilities to infiltrate computers and networks. You can significantly reduce the risk of an attack by regularly updating all of your software and browsers. Make it a habit to check the software developer’s website for any security patches. Better yet, hire a managed IT services provider to keep your system up to date. Closely monitor your network Regularly conduct security checks using network security tools like intrusion prevention systems that detect and contain suspicious or malicious network activities before they cause problems. Consider using bandwidth management software to enable you to observe user behavior and detect abnormalities that could indicate an attack, such as large data transfers or a high number of downloads. Hide your online activities Use a VPN and your browser’s private browsing feature to hide you and your team’s online activities. You can also block social media sites from your office network, as these are often used as share points of links to infected sites. Watering hole attacks can be devastating to businesses of all sizes. By staying informed and taking steps to protect your business, you can minimize the risk of becoming a victim. Contact us today to learn more ways to keep your business safe from watering hole attacks and other cyberthreats. Published with permission from TechAdvisory.org. Source.
How to easily transfer files from an Android device to a PC or Mac

There may be times when you need to transfer files from an Android device to a PC or Mac. This article will discuss several ways to do that. Through a USB cable Using the USB cord that came with your phone is probably the most convenient way to transfer files to your computer. If your phone has a newer USB Type-C-to-Type-C cable and your desktop or laptop does not have a USB-C port, you’ll need to use a hybrid USB-C cable or a USB-C cable adapter. You can easily find these in your local hardware or computer store. The rate of data transfer is determined by the type of cable and storage you have on both devices. For example, a phone with an embedded MultiMediaCard will transfer data slower than one with Universal Flash Storage. Additionally, moving files to a computer with a solid-state drive is faster than on those using traditional hard drives. To transfer files from your Android device to your Windows or Mac via a USB cable, follow these steps: Windows Connect your device to your PC using the USB cable. Tap on the notification that will appear to go to the USB Preferences menu. Tap on the File Transfer option. Select from one of the provided options on what to do with the connected device, including: Import photos and videos – When you choose this option, Windows will automatically search and display all the videos and images stored on your device. You can use the checkbox to choose which ones you want to transfer to your computer. Windows will also assign a default destination folder where your photos and videos will be saved, but you can change it by clicking on the Change destination option below the default folder destination. Open device to view files – Choosing this option will bring up File Explorer. From there, you can choose the files on your device that you want to transfer by copy-pasting them or simply dragging them to a specific folder. Once the file transfer is complete, disconnect the USB cable from your computer. Mac To transfer files from your device to a Mac computer using a USB cable, you first need to install an official Android file transfer app. Once you’ve done that, simply follow these steps: Connect your device to your Mac using the USB cable. When the USB Preferences notification appears, choose the File Transfer option. Open the Android file transfer app. From there, you can transfer your files by dragging them to the Finder window. Via Bluetooth If you don’t have a USB cable, you can use Bluetooth to transfer your file. However, the transfer speed is significantly lower via this method. Here’s how to transfer your files using Bluetooth: Enable Bluetooth on your Android device and PC or Mac. Search for available devices. When you find your device, tap on it to pair with it. Your computer will ask you to confirm a PIN before both devices can be connected. There’s an extra step you have to take if you’re using a Mac. Go to System Preferences > Sharing and choose the Bluetooth Sharing option. From there, you can set the default folder where the files will be stored. Tap on the files on your device you want to transfer, then tap the Share icon and choose Bluetooth. Choose your PC or Mac from the list of connected devices. On a PC, right-click the Bluetooth icon on the Taskbar and select Receive a File. Windows will automatically save the files in the Documents folder. On a Mac, the files you shared will be sent to the folder you specified in the Bluetooth Sharing option. If you follow these steps, you’ll be able to transfer your files in no time. If you want to learn more Android tips and tricks, call our specialists today. Published with permission from TechAdvisory.org. Source.
5 Reasons SSDs are better than HDDs for Macs

Solid-state drives (SSDs) are fast becoming the standard for data storage because of their many advantages over hard disk drives (HDDs). Here are the top five reasons SSDs are better than HDDs for Macs. SSDs are more reliable All types of disk drives are more likely to fail with age, but SSDs are more resistant to age-related degradation than HDDs. This is because most modern SSDs use NAND flash memory, which is not as susceptible to the wear and tear that HDDs experience with their spinning disks. Moreover, HDDs utilize magnets to write data, so exposing your Mac to a powerful magnet may erase all of its contents. This is an unlikely scenario with SSDs since they don’t have parts with magnetic coatings that can be easily damaged by a magnetic field. SSDs are more durable HDDs have delicate moving parts like drive platters and read arms, which are prone to breaking if you drop your Mac or if you bump or jostle it around too much. SSDs, on the other hand, have no moving parts, so they’re much more resistant to physical damage. In addition, SSDs can withstand higher temperatures than HDDs without losing data. This means that SSDs are less likely to be affected by heat buildup from extended use or from being stored in a high-temperature environment. Finally, SSDs have a longer life span than HDDs. Although consumer SSDs have a limited number of reads and writes, they can still last for 700 TB of writes before failing. To give you some perspective, 40 GB of data every day for 50 years would amount to 700 TB. In other words, you won’t have to worry about overusing your SSD anytime soon. SSDs are faster The data access speeds of HDDs are limited by the fact that they have spinning disks. The data on an HDD is stored on these disks in sectors and tracks, and the read/write head has to physically move to the correct location on the disk in order to access the data. This physical movement takes time, which means that it can take a while to start up your computer and load files. By contrast, SSDs store data on interconnected flash-memory chips. These chips can be accessed much faster than the spinning disks of an HDD, which means that your Mac will boot up more quickly and files will load faster. This allows you to perform data-intensive tasks without waiting for your computer to catch up. SSDs are quieter HDDs tend to produce a fair amount of noise because of their spinning disks. This noise is generally not loud enough to be a bother, but it can be noticeable in quiet environments. Meanwhile, SSDs don’t make any noise at all, mainly due to their nonmechanical nature. Because there are no moving parts, a Mac with an SSD is generally quieter, even when it’s performing intensive tasks. SSDs are more energy-efficient SSDs consume far less power than HDDs and, as a result, need considerably less energy to function. Even when operating at full speed, SSDs use roughly 50% less energy than HDDs. This is also thanks to the fact that SSDs have no moving parts that must be powered in order for them to read, write, and access data. This lower power consumption can translate into longer battery life for laptops. So, if you’re looking for a MacBook that will last through a long flight or an all-day meeting, you’re better off getting one with an SSD. Overall, it’s clear that SSDs have a lot of advantages over HDDs. A reliable SSD will improve your Mac’s performance, which can also result in better productivity and efficiency. If you’re ready to upgrade your Mac with an SSD or have any questions about data storage, call us today. Published with permission from TechAdvisory.org. Source.
Easy tips to increase your computer’s longevity
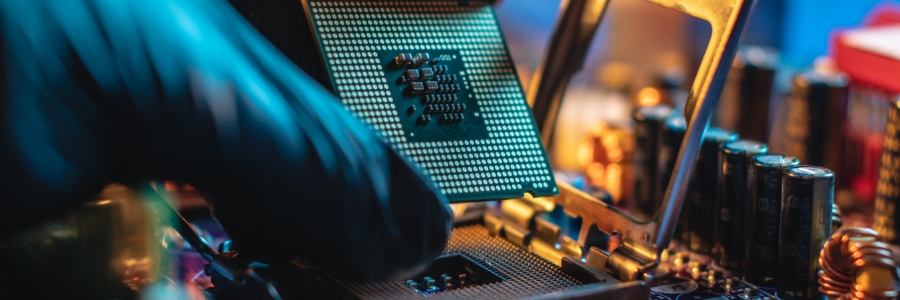
Computers are expensive, and like any large investment, you want to make sure you get your money’s worth. Prolonging the life span of your computer will save you both money and frustration down the line. Here are tips to keep your computer running smoothly for years to come. Clean and cover your computer Dust and dirt are your computer’s number one enemy. They can get caught between the keys and other moving parts, which will then cause problems with how the computer operates. To avoid any performance issues or long-term damage, it is best to clean your computer regularly and be sure to cover it when not in use to prevent dust and dirt from building up. Use canned air to clear out any dirt, especially from fans. If these get blocked with too much debris, the fan’s ability to cool down the computer decreases, which then raises the risk of overheating. When cleaning computer screens, only use the appropriate screen cleaners. Never use window cleaners because they contain ammonia, which can dull and damage the screen. Avoid eating food or placing drinks next to your computer. Food particles can get stuck between the keys on your keyboard, making it difficult to type, and spilling drinks on your computer can cause it to short circuit. Keep your computer cool When a computer is switched on, it produces heat. If the temperature is not regulated properly, a computer can overheat, damaging its processor, graphics card, and other internal components. This can cause your computer to malfunction and eventually break down. To prevent this, place your computer in a well-ventilated room and away from direct sunlight. Make sure the cooling fans and heat sink are working properly. If you’re living in a hot climate, you may need to purchase additional cooling fans or use your computer in an air-conditioned room. Update your computer’s operating system and programs Updating your operating system is essential to maintaining optimum system efficiency. Updates include patches, security fixes, and software/driver updates that make your computer compatible with the latest web applications and software. It’s essential to update your antivirus software as well. Antivirus updates contain new malware/virus definitions that will help you identify and stop new online threats. Perform disk maintenance regularly Traditional hard drives can crash from file system errors, bad sectors, improper shutdowns, and other issues. If the corruption is severe enough, it could damage files beyond repair and prevent your computer from starting. Performing regular error checks will help you spot potential hard drive issues before they blow out of proportion. You should also run Disk Cleanup and Disk Defragmenter at least once a month. Disk Cleanup will remove unnecessary files that take up hard disk space, while Disk Defragmenter consolidates fragmented files into one space to help increase computer performance. Invest in surge protectors Power surges, regardless of magnitude, can damage or completely destroy your computer’s components. Using a surge protector is a good way of protecting your computer against sudden power surges. When shopping for a surge protector, check the joule rating. It indicates how much energy the surge protector can handle before it needs to be replaced. The higher the number, the better. You should also look for a surge protector with an auto-shutoff feature. In the event of a power surge or other electrical problem, the surge protector will automatically shut down to protect the devices connected to it. Switch to solid-state drives (SSDs) Unlike hard drives, solid-state drives have no moving parts, making them more resistant to wear and tear and accidental drops. The absence of moving parts also means SSDs require less power to operate compared to hard drives. SSDs are also 100 times faster than traditional hard drives. This results in faster boot and application loading times and improved system responsiveness. Following these tips will help extend the life of your computer. If you want to learn more, give our specialists a call today. Published with permission from TechAdvisory.org. Source.
How to protect your business from TDoS attacks

Small businesses are increasingly moving from traditional telephones to Voice over Internet Protocol (VoIP) to save on costs. While VoIP offers many benefits, an unsecure system can leave your business vulnerable to a new kind of attack called telephony denial-of-service (TDoS). In this blog post, we will discuss what TDoS is and how you can protect your VoIP system and your business against it. What is TDoS? A denial-of-service attack aims to crash a system by bombarding it with an overwhelming number of requests, forcing the targeted system to shut down eventually. A TDoS attack is a subcategory of DDOs that’s leveled at VoIP systems. Alarmingly, this attack is commonly used against hospitals and 911 phone lines. Some TDoS attackers even demand a ransom to halt the attack, which is similar to how ransomware works. They take advantage of cryptocurrencies and caller-ID spoofing to make it difficult to identify attackers. TDoS attacks generally utilize fewer resources than the DoS attacks that are designed to cripple IT systems, which include networks, servers, and software. At its most basic, a TDoS attack requires only an automated phone dialer that repeatedly calls a target phone number and hangs up. That very simple strategy can stop anyone else from getting through the line. What organizations need to do When defending against such a threat, your first instinct may be to lock down your VoIP system with complicated security measures. However, doing so can do more harm than good, as most businesses are unable to efficiently operate if they can’t communicate with their customers, business partners, and other third parties. Although VoIP may be a digital resource similar to other components within your IT systems, the very nature of VoIP phone lines makes it impossible to hide them behind firewalls and other protections. Fortunately, there are new security protocols that can protect your communication infrastructure against those who try to use force to gain access to your directory information. When properly implemented, these protocols can also identify, reroute, and filter calls coming from known attackers. Any business that relies on VoIP for communication needs to take steps to protect its VoIP system against TDoS attacks. Such attacks can greatly disrupt operations, and in some cases, even result in financial loss. By working with a reputable VoIP provider and taking proactive measures to secure your system, you can ensure that your business is able to weather any TDoS storm. Don’t let an attacker take away your business’s ability to communicate securely with customers and partners Contact our IT experts and take the next steps to secure your VoIP system today. Published with permission from TechAdvisory.org. Source.
Viva Insights: An essential business productivity tool

Viva Insights uses the power of data and analytics to help businesses of all sizes improve their employees’ productivity. Let’s learn more about this business productivity tool and how it can benefit your organization. How does Viva Insights work? Viva Insights shows users personalized recommendations that can help them do their best work. By analyzing Microsoft 365 data, such as emails, calls, meetings, and chats, it can generate insights for building better work habits that help people become more productive and improve their well-being. The tool can gather and provide the following information: Personal insights help individual users understand how they work and what they need to do to improve their performance. Teamwork habits let you determine work habits that may cause burnout, such as having too many meetings, too little focus time, and frequent after-hours work. This way, team members can learn how their habits affect the rest of the team and how they can help their colleagues balance productivity and well-being. Organization trends provide managers and business leaders visibility into how the work culture is impacting employee productivity and well-being. They can use the recommendations to make necessary improvements. Advanced insights can help company leaders address vital issues about organizational resiliency, such as how work affects their people and the business. What are the other features of Viva Insights? Aside from providing important insights, Viva Insights also has a few handy features that can help employees improve their work life. These include: Stay connected: This feature allows users to interact better with their colleagues. It also suggests one-on-one meetings with managers or colleagues, sends meeting reminders, and reminds users to RSVP when needed. Protect time: Viva Insights users can schedule focus time right on the app. Do Not Disturb functions are automatically enabled to prevent distractions. Send praise: Users can acknowledge their team’s and colleagues’ hard work by sending them praise via private chat or a Teams channel. Reflect: This feature encourages workers to focus on themselves. Users can create reminders to see how they are feeling and access their reflection history to determine how their feelings have evolved. Users can share this data with their managers and other company leaders. Headspace: Users can access the mindfulness app Headspace within Microsoft Viva to help them start their day grounded, relax before a big presentation, or focus before starting a project. They can also use it to close out their day with a mindfulness exercise during their virtual commute. Take a break: This feature encourages users to take several deep breaths for one minute. Microsoft To-Do: This task management application helps users better manage their tasks and commitments. To make sure you reap all the benefits of Viva Insights, give us a call. We’ll be more than ready to help you set it up and tailor it to your business’s needs. Published with permission from TechAdvisory.org. Source.
