3 ways to browse the net safely at work
Amidst the current climate of malware, hacks, and phishing scams, the internet really isn’t safe for any company that doesn’t take precautions. Without safeguards, browsers that you or your employees use are vulnerable to cyber attacks that may cripple productivity and profit. There are wise steps that every company should take to browse the net safely. Data stored on desktops, servers and in the cloud, doesn’t make it safe. If anything, it makes it available to anyone who has the desire and capabilities to hack into your system and cause mayhem for your business operations. One thing you should be doing to protect your data – and your company – is to make use of privacy-protecting browser extensions. Depending on the nature of your business, both you and your employees are likely to be online at least some, if not all, of the working day. What are some of the browser extensions that can make the experience more secure? Prevent browser tracking If you don’t like the idea of a third party (reputable or otherwise) being able to track your browsing habits, try installing a tool for private browsing. These programs offer protection against tracking by blocking third-party cookies as well as malware. Some extensions also boast secure Wi-Fi and bandwidth optimization and can guard against tracking and data collection from social networking sites such as Twitter, Facebook or Google+. Blocking adverts While online ads may seem harmless, the truth is they can contain scripts and widgets that send your data back to a third party. A decent ad blocking program will block banner, rollover and pop-up ads, and also prevent you from inadvertently visiting a site that may contain malware. Many blockers contain additional features such as the ability to disable cookies and scripts used by third-parties on a site, the option to block specific items, and even options to ‘clean up’ Facebook, and hide YouTube comments. The major blockers work with Google Chrome, Safari, and Firefox and you’ll be able to find everything from user-friendly solutions to more advanced tools that are customizable down to the tiniest degree. Consider installing a VPN Unfortunately, browser tracking, malware, and adware are not the only internet nasties that you need to be concerned about. but the good news is that there a number of other extensions that you can download to really get a grip on your online safety. A VPN (Virtual Private Network) is something else to consider. VPNs encrypt your internet traffic, effectively shutting out anyone who may be trying to see what you’re doing. Commonly used in countries where the internet is heavily censored by the powers that be, a VPN allows for private browsing as well as enabling users to access blocked sites – in China’s case that’s anything from blogs criticizing the government to Facebook and Instagram. There are hundreds of VPNs on the market so do a little research and find one that suits you best. Finally, it goes without saying that having anti-virus and anti-malware software installed on your PC, tablet, and even your smartphone is crucial if you want to ensure your online safety. Is browsing at your workplace secure? Would you like a more comprehensive security system for your business? We can tell you all about it and help your business protect itself from online threats. Get in touch with us today. Published with permission from TechAdvisory.org. Source.
The benefits of technology business reviews

Small- and medium-sized businesses don’t have the time to maintain IT infrastructure, let alone assess whether it’s still driving value for the company. However, if you want to ensure everything runs smoothly, it’s important to be proactive and conduct technology business reviews when you can. What is a technology business review? A technology business review reveals the strengths and weaknesses of your company’s IT framework. It’s often performed by a third-party IT consultant who will give an objective assessment of your technology and provide recommendations to help meet your goals. If done properly, technology business reviews allow you to: Save money Every review starts with a cost-benefit analysis to determine whether a solution you’ve implemented is worth the continued investment. If there are technologies costing you a fortune in management and maintenance fees, consultants will advise you to cut them from your budget. The best ones will even recommend cost-effective alternatives so you can do more with less. Increase productivity System-wide reviews of your IT infrastructure show you what processes are hindering operations and propose solutions that let you work faster and smarter. For example, if employees are mainly sharing files via email, consultants might suggest cloud collaboration platforms like Office 365 or G Suite that store data in a centralized location for seamless file sharing. Enhance security and compliance Technology business reviewers also uncover security risks within your business. Consultants scan for missed patches, poorly configured networks, and other software vulnerabilities that make it easy for cybercriminals to hack your systems. They’ll then compile their findings to create a more robust defense strategy, usually one that involves implementing advanced solutions like intrusion prevention systems, file access restrictions, and patch management software. If you operate a business that’s subjected to data regulations like HIPAA or PCI-DSS, consultants will also pinpoint IT practices and solutions that are noncompliant and customize a strategy that ensures the privacy, integrity, and availability of your data. Implement technologies that fit Considering that new technologies are released at a breakneck pace, it’s important you pick the ones that make sense for your operation, its goals, and the bottom line. Technology business reviews keep you up to date on the latest technology trends and gauge the impact of implementing them, so you can make informed decisions. Whether your goal is to increase profits, productivity, security, or all of the above, technology business reviews can put you on the right track. Our seasoned IT consultants can conduct these reviews for you and develop a strategy that gives you an edge over the competition. Just give us a call. Published with permission from TechAdvisory.org. Source.
Is Google’s newest smartphone right for you?

Companies that want their employees to have the best mobile devices for work usually choose one of three devices, a Pixel, one of the Galaxy S phones, or an iPhone. The Pixel phone is Google’s flagship device, and although it’s price isn’t much different from the competition, it’s packed with business benefits. Let’s review the latest iteration. Models and pricing The Pixel 3 comes in two models, each with two price points depending on how much storage you need. The smaller device has a 5.5-inch screen with a slightly higher resolution, 2160×1080, than standard HDTVs. It’s $799 for 64GB of internal storage and $899 for 128GB. The Pixel 3 XL comes with a jump in screen size and resolution, 6.3 inches at 2960×1440. The XL also comes with a slightly bigger battery to power the larger screen. It’s $899 for 64GB of internal storage and $999 for 128GB. Google Assistant If you or your employees use Google’s AI assistant to schedule meetings, send emails, or set reminders, the Pixel delivers a few features you won’t find anywhere else. For one, you can squeeze the side of the phone a bit harder than usual to summon the voice assistant. Pixel 3s also come bundled with Google’s Buds headphones, which make it easier to interact with Assistant without looking at the screen. Your notifications, reminders, and emails can be read to you as they come in and voice commands let you respond to text and email messages. The voice assistant can even answer spam phone calls on your behalf, showing a live audio transcription on your screen in case you decide to take the call. Software Having the latest version of Android installed on your phone is extremely important. It keeps you safe from malware designed for mobile devices and vulnerabilities in wireless networks, such as KRACK. If your smartphone is manufactured by a company other than Google, you have to wait for that company to release a modified version of Android for that device. Even big-name manufacturers like Samsung take months to release these updates. With the Pixel 3, the latest version of Android — along with all its feature and security updates — is always available to you on day one. Ancillary features Google’s flagship phone is IP68 water and dust resistant, which is great if you or your employees work in harsh environments. Pixel 3s also support wireless charging so you never have to plug in your phone again. Just set it down on a charging mat to juice it up. Could you get through an entire day of work without your smartphone? Probably not. The Pixel 3 is an excellent option for staying productive anywhere you need to be, especially if you’re already using the Google Assistant. If you have any questions about optimizing Android devices for your work environment, give us a call today. Published with permission from TechAdvisory.org. Source.
Container facts you’re misunderstanding

Virtualization and container technologies are confusing topics in their own right, and comparing and contrasting them is even harder. To understand the differences between container and virtualization technologies, it’s best to clear up some commonly misunderstood information on how they work. Containers are made up of the bare minimum hardware and software requirements to allow a specific program to run. For example, if you want to give employees access to a single Mac-based server application, but everything else you run is in Windows, it would be a waste to build a new machine for just that program. Containers allow you to partition just the right amount of hardware power and software overhead to run that Mac program on your Windows server. Misconception #1: Containers require virtualization Previously, containers could only be created and managed in the Linux operating system (OS). This meant complicated and sometimes unreliable improvisation was required to benefit from container technology on Windows and Mac servers. First, you would need to virtualize a full-fledged Linux installation on your Windows or Mac server, and then install container management inside of Linux. Now, container management software can run on Windows and MacOS without the confusing multi-layer systems. Misconception #2: There is only one container vendor Traditional virtualization technology, which creates entire virtual computers rather than single-application machines, allowed two decades for vendors to enter the market and improve their offerings. Containers, however, didn’t break into the mainstream until a few years ago. Fortunately, there are still more than enough container vendors. Docker dominates the industry and headlines, but there are at least a dozen other programs to choose from. Misconception #3: You can’t create and manage containers in bulk Orchestrators are separate programs that allow you to scale up your use of containers. If you need to partition more hardware power so more users can use a container, or if you need to create several identical containers, orchestrators make that possible. Misconception #4: Containers are faster than virtual machines Obviously, virtualizing an entire operating system and the hardware necessary to run it requires more management and processing requirements. A lot of people tend to think this means containers are faster than virtualized machines. In reality, containers are just more efficient. Accessing a container is as simple as opening it and using the application. A virtualized machine, however, needs to be booted up, a user needs to log in to the OS, and then you can rummage through folders to open an application. Most of the time containers are faster, but there are instances when that’s not true. Virtualization and containers are complicated technologies. For now, just remember that 1) Virtualization and containers are separate technologies, each with pros and cons, and 2) you have plenty of software options to manage containers (sometimes in bulk). For anything more specific than that, give us a call! Published with permission from TechAdvisory.org. Source.
Don’t be a VoIP eavesdropping victim

In the digital world, eavesdropping is a form of cyberattack where voice over internet protocol (VoIP) phone calls are intercepted and recorded, usually to glean personal or business information. Since it does not affect call quality, it’s hard to tell if you’ve been a victim of eavesdropping. Ensure that you never become one by implementing these security strategies. Change the default configurations Using your VoIP phones without changing the default configurations can be the worst mistake you can make. Doing so means bad guys can search vendor documentation for things like default usernames and passwords. Depending on your VoIP solution, you should have the option of changing the default configurations on your VoIP handsets. Otherwise, you should come up with a manual process to change default configurations before rolling phones out to your staff. Get updates from your handset vendor In 2015, Cisco detected vulnerabilities in their VoIP phones that enabled attackers to listen in on phone conversations. Cisco quickly issued security alerts, but if they hadn’t, several companies would have fallen victim to VoIP eavesdropping. The lesson here is you must regularly monitor advisories from your hardware vendor or work with an IT provider that does so for you. Without proper monitoring, you won’t know how susceptible your corporate VoIP phones are to being eavesdropped. Update session border controllers Another way to combat VoIP eavesdropping is to constantly update your session border controllers (SBCs). By doing so, you’ll be updating your VoIP’s antivirus software, so your systems are better protected from constantly evolving cyberthreats. Routine SBC updates are essential for securing SIP trunking as well as responding to new threats. Encrypt VoIP calls If you work in a regulated industry like healthcare or finance, encrypting VoIP calls is essential to staying compliant. Work with your VoIP provider and auditors to determine the best encryption options for your communications infrastructure. Many cloud VoIP providers offer call encryption guidelines, and some even offer it as a premium service. Build a hardened VoIP network Make sure your VoIP network includes: IP private branch exchange (PBX) using minimal services, so that the hardware can only power the PBX software Firewalls with access control lists set to include call control information Lightweight Directory Access Protocol lookup, and signaling and management protocol Reinforced endpoint security with authentication at the endpoint level To effectively combat VoIP eavesdropping, businesses need to take a holistic approach. This includes policies, deployment, and security practices that will keep malicious agents out of your network. Feel free to contact us for further information on how to protect your business. Published with permission from TechAdvisory.org. Source.
Office 365 beefs up anti-phishing measures

There are plenty of things to love about Office 365. For a small monthly fee, it gives you the latest cloud-based version of Microsoft Office apps and robust communication tools that improve collaboration and productivity. But it’s also an extremely secure platform that can defend against the most cunning phishing attacks. Effective anti-phishing solutions must be able to recognize the key elements of a phishing attack, which includes spoofed (or forged) emails, compromised accounts, unsafe links, and harmful attachments. In April 2018, Microsoft upgraded Office 365’s Advanced Threat Protection (ATP) features so it can better detect these elements and prevent a wide variety of phishing scams. These enhancements include: Anti-impersonation measures – ATP will now look for potential phishing indicators in an email, including the sender’s address, name, and links, to identify whether the user is being impersonated. You can specify high-profile targets within your organization, such as managers and C-level executives, so Office 365 can protect these users from email impersonation. Office 365 also utilizes machine learning to analyze a user’s email patterns and flag suspicious contacts that have had no prior correspondence with your company. Anti-spoofing technology – This feature reviews and blocks senders that disguise their true email address. You can even enable safety tips that flag certain email domains that have strange characters. For instance, if your real domain is Acme.com, a spoofed domain could be Acḿe.com. Email link scanning – Office 365 launched Safe Links, which scans emails for fraudulent links and redirects users to a safe page in case it does contain harmful materials. This feature also applies to email attachments, ensuring you’re protected against all types of phishing scams. Due to these improvements, Office 365 had the lowest phish rate among other well-known email services between May 1 and September 16, 2018. The company has stopped over five billion phishing attempts and protected users against seven billion potentially malicious links. If you’re looking for a secure email platform, Office 365 is the best option for your business. That said, it’s not a substitute for good security awareness. No matter how secure Office 365 is, employees still need to be adequately trained to recognize a phishing email when they see one. Hackers are constantly changing their tactics to evade Office 365’s detection systems, so it’s important that everyone is alert at all times. If you need a well-fortified email service, we can implement and manage Office 365 for you. We even offer practical security advice to make sure your business, employees, and assets are safe and sound. Contact us now. Published with permission from TechAdvisory.org. Source.
4 handy Cortana commands for you
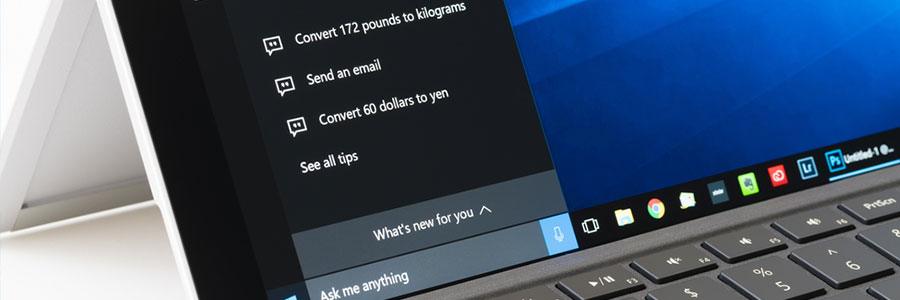
You’ll find Cortana, Microsoft’s voice-activated personal assistant, extremely helpful for daily tasks, like rescheduling meetings, drafting an email, or dealing with several other time-consuming work. Learn how to use the following Cortana commands to make life so much easier for you. Hey, Cortana Before asking her to do anything, we need to get Cortana’s attention by clicking or tapping the Cortana button on the taskbar. If you do not see Cortana on your taskbar, right-click the taskbar and go to Cortana > Show Cortana icon. To enable Hey, Cortana, simply say ‘Hey, Cortana,’ followed by your question. If you’re using a Windows Phone, you can press and hold the search button to activate Cortana. Basics tasks If you want to launch a program or open a website, simply use the word ‘Launch’ or ‘Open’ followed by the website’s name. Make notes by uttering the words ‘take a note’ or ‘note it down’. As for making drafts, start with ‘Write an’ followed by ‘email’ or ‘text,’ and end with the contact name and the message itself. Lastly, ‘Show me emails from [contact]’ will display all the emails sent from the specified contact. Scheduling/Reminders It’s important for small- and medium-sized business owners to stay on top of their schedules. Take a glance at your calendar events with commands such as ‘How’s my schedule looking?’ or ‘What do I have next week?’. Add or move appointments with ‘Add’ or ‘Move’ followed by the appointment and time. Reminders are easily scheduled by uttering the words ‘Remind me’ followed by whatever you need to be reminded about and when. Search If you can’t locate the file you need, don’t worry. By asking Cortana to ‘Find’ a document, video, or picture on your device from a specific time frame, she will sift through everything quickly to find what you need. You can easily initiate search queries with ‘Can you find’ followed by whatever you are looking for. You can even look at basic search results without having to open a browser window: Simply ask whatever question you have and enjoy combing through the results. Window’s voice-activated personal assistant, Cortana, helps you accomplish daily tasks with ease and efficiency — but only if you use the right commands. If you have further questions or would like to know more Cortana commands, feel free to contact us. We’re ready to help! Published with permission from TechAdvisory.org. Source.
Is your IT security proactive?

Do you spend hours obsessing about the inner workings of DNS-layer security, intrusion prevention systems, and data encryption? If you’re not a managed IT services provider (MSP), you probably don’t. Instead, you’re probably looking for a business partner to manage those nitty-gritty details for you. However, there’s one thing you really ought to know: What exactly are “proactive cybersecurity” measures? Understand the threats you’re facing Before any small- or medium-sized business (SMB) can work toward preventing cyberattacks, everyone involved needs to know exactly what they’re up against. Whether you’re working with in-house IT staff or an MSP, you should review what types of attacks are most common in your industry. Ideally, your team would do this a few times a year. Reevaluate what it is you’re protecting Now that you have a list of the biggest threats to your organization, you need to take stock of how each one threatens the various cogs of your network. Map out every company device that connects to the internet, what services are currently protecting those devices, and what type of data they have access to (regulated, mission-critical, low-importance, etc.). Create a baseline of protection By reviewing current trends in the cybersecurity field and auditing your current technology framework, you can begin to get a clearer picture of how you want to prioritize your preventative measures versus your reactive measures. Before you can start improving your cybersecurity approach, you need to know where your baseline is. Devise a handful of real-life scenarios and simulate them on your network. Network penetration testing from trustworthy IT professionals will help pinpoint weak spots in your current framework. Finalize a plan All these pieces will complete the puzzle of what your new strategy needs to be. With an experienced technology consultant on board for the entire process, you can easily synthesize the results of your simulation into a multi-pronged approach to proactive security: Security awareness seminars that coach all internal stakeholders – train everyone from the receptionist to the CEO about effective security practices such as password management, proper mobile device usage, and spam awareness Front-line defenses like intrusion prevention systems and hardware firewalls – scrutinize everything trying to sneak its way in through the borders of your network Routine checkups for software updates, licenses, and patches – minimize the chance of leaving a backdoor to your network open Web-filtering services – blacklist dangerous and inappropriate sites for anyone on your network Updated antivirus software – protect your data and systems against the latest and most menacing malware As soon as you focus on preventing downtime events instead of reacting to them, your IT infrastructure will increase your productivity and efficiency to levels you’ve never dreamed of. Start enhancing your cybersecurity by giving us a call for a demonstration. Published with permission from TechAdvisory.org. Source.
Secure your Mac computer in 6 easy ways

If you’re a Mac user, data privacy and security should be your #1 priority. Without the right security measures, you’re inviting cybercriminals to steal your critical data. Are you willing to take the risk? Secure your computer and fortify your defenses with these six tips. The basics First, let’s start with the basics and head over to the Security & Privacy pane in System Preferences. Here, you’ll find the General, FileVault, Firewall, and Privacy tabs, which control various aspects of security. To change your security settings, click on the padlock icon on the bottom of the screen and type in your username and password. Firewall Enabling the firewall will block unwanted incoming network connections. All you need to do is click Firewall in the System Preferences > Security & Privacy pane, click the padlock icon on the bottom left, enter your username and password, and click Turn On Firewall. Don’t forget to enable Stealth Mode by clicking Firewall Options then clicking Enable Stealth Mode in the dialog box — this makes your computer invisible on public networks. Passwords Make sure to set strong passwords for your user accounts if haven’t already. To do this, go back to the General section of the Security & Privacy settings. In this section, you should also consider setting the Require Password field to “immediately.” This will require you to re-enter your login credentials to unlock your Mac when it goes to sleep mode or when a screensaver is on. Automatic login It’s best to disable this function, especially if you are using a mobile Mac. If your Mac gets stolen, you don’t want to give thieves a free pass to your private data. Applications At the bottom of the General Settings tab, there are three options that authorize which apps can run on your Mac. The safest option is to allow only apps from the App Store to run, and the least secure option is to allow apps downloaded from unauthorized stores. Get the best of both worlds by choosing the option of running apps from the App Store and from developers known to Apple. FileVault The FileVault tab enables you to encrypt all the files in your account. To decrypt them, you must enter either your account password or the recovery key you created when you switched FileVault on. It might be tedious to type in a password every time to access a file, but it helps keep your vital data under lock and key. In this digital age, ensuring the protection of all your devices is crucial to your business’s success. Feel free to give us a call and we’ll help prepare your business for choppy waters. Published with permission from TechAdvisory.org. Source.
Ways IoT will change the business world

The Internet of Things (IoT) is a network of vehicles, appliances, and devices embedded with actuators, connectivity, software, electronics, and sensors that allow users to connect and swap data. The business world is steadily changing with the implementation of IoT in the following methods. Improved logistics With IoT sensors, supply chain management and order fulfillment processes improve markedly to meet customer demand. For example, sensors on delivery containers and trucks in transit give managers real-time status updates, allowing them to track their items and ensure they reach the right location at the right time. Streamlined inventory IoT also presents automation opportunities for businesses that need to manage and replenish their stock. When data recorded from IoT devices are tied to your enterprise resource planning (ERP) system, you can accurately monitor your inventory, analyze purchase and consumption rates of a particular product, and automatically reorder items when IoT sensors detect that supply is running low. This minimizes out-of-stock incidents and prevents excess stock build-up. Fast payment Given how most payments are done electronically via point-of-sale systems or the internet, IoT has the potential to revolutionize the way businesses process transactions. For example, ApplePay not only allows users to purchase goods and services using the usual smartphone applications, but through state-of-the-art wearable technology as well. Soon, IoT devices might even allow restaurants and retailers to register or charge their customers the moment they walk through the door. Market insight Businesses that can make sense of IoT-collected data will gain a competitive edge. Marketers, for example, can gather valuable insight into how their products are used and which demographic is utilizing them the most. This information can then inform future marketing efforts and give businesses more focused direction on how to improve their products and services for their customers. Although businesses will certainly face many challenges in implementing the Internet of Things, those who overcome them will reap all the benefits of this burgeoning technology. Want to know if an IoT deployment is right for your business? Contact our certified IT consultants today. Published with permission from TechAdvisory.org. Source.
